Starting with Ghidra Framework
About Ghidra, when you start the framework, you should create a project and a workspace:
Then, we can import files, for example PE files:
Ghidra CodeBrowser
Once PE file is imported, CodeBrowser can be launched:
Initially, PE headers are parsed but code is not analyzed, the framework asks you if analyzers should be launched, and what analyzers should be launched. This is the list of analyzers (they are marked the analyzers that are marked by default):
Once analyzers finish, CodeBrowser interface is like this:
Code is fully decompiled and while you browse each function, the decompiled code is showed in the right window.
Browsing Code
Browsing code is similar to IDA, you can double-click a name to jump there (for example double-clicking the destination of a call <destination>, would take you to the destination function). You can move easily to the previous location with Alt+left (equivalent to Esc in IDA) and next location with Alt+right (equivalent to Ctrl+Enter in IDA).
Other navigation options:
You can search for text, like IDA Alt+t, however (and I found this an interesting characteristic), you can select where do you want the text is going to be searched:
Find TrickBot Config Xor-layer Decryptor
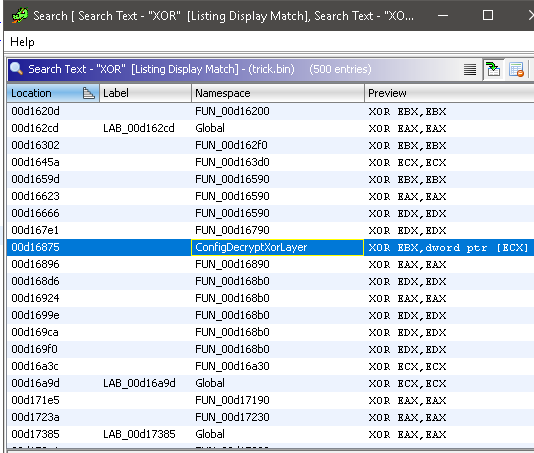
For example, we can try to search for XOR instructions, and we get a list of matches:
In the analyzed sample (a trickbot from early 2019), if we look for XOR instructions, we can find easily some XOR instructions modifying memory, and one of them belongs to the function that decrypts the XOR layer of the trickbot config:
(Btw, as we can see in the image, when you select with the mouse a line in the disassembly window, the equivalent line is highlighted in the decompiled window).
Using references to find more interesting parts of the code
Once you have located an interesting point in the code, you can show a tree of calls to that point:
The tree makes easy to follow the incoming or outgoing references to the interesting function:
Additionally, you could highlight (select) back or forward refs to an address in the disassembly and decompiled windows.
TrickBot ECS signature and Config Xor Decryptor
By using the call trees, we can find easily the functions that decrypts the XOR layer of the elliptic curve signature or the XOR layer of the TrickBot Config:
In addition, you can open a function graph window, similar to IDA graphs. Here is the XOR decryptor loop of TrickBot:
You can move easily on the graph, and zoom in/out with the mouse wheel:
TrickBot Strings Decryptor
About strings.. All the strings used by the newer versions of TrickBot are encrypted. While IDA was able to construct a nice table of strings that makes easy to find the decryptor:
Ghidra were not able to identify all the strings and construct a nice table, it is much lesser intuitive:
Maybe I missed something with Ghidra, but I selected the option Analysis->One shot->Ascii Strings, and these are the results. This makes difficult, for example, to find strings' decryptors.
Conclussion
in spite of the fact that I really love IDA (and WinDbg), I liked this framework, and I will continue using it.
















No comments:
Post a Comment