- Original Packed Sample: 89782B6CDAAAB7848D544255D5FE7002
- Source Url: http://a4.doshimotai[.]ru/pxpx.exe
- Info Url: VxVault URLhaus
- Automatic Generated Report: PepperMalware Report
- Virustotal First Submission: 2019-03-18 22:28:20
- Any.Run Analysis: Here
- Any.Run Tags: Evasion, Trojan, Rat, Quasar
- My Classification: I named it GrandSteal because of the internal .Net classes names (if you have any information about any well-known family that this malware belongs to, please, tell me and I will update this post)
- Decompiled Source Code: PepperMalware Github
Analysis
- 1. Loader
- 2. Unpacked Modules
- 2.1. List of Unpacked Modules
- 2.2. Stealer
- 2.2.1. Chromium Stealer
- 2.2.1.1. Cookies
- 2.2.1.2. Credentials
- 2.2.1.3. Autofills
- 2.2.1.4. Credit Cards
- 2.2.2. Wallets Stealer
- 2.2.3. Files From Personal Directories Stealer
- 2.2.4. Discord Software Stealer
- 2.2.5. FileZilla Stealer
- 2.2.6. Gecko Stealer
- 2.2.7. RDP Stealer
- 2.2.8. Telegram Stealer
- 3. Yara Rule
- 4. Strings of the Main Unpacked Module
1. Loader
- The sample is not signed.
- Version Info:
- Product Symantec© 2019
- Description pxpx.exe
- Original Name pxpx.exe
- Internal Name pxpx.exe
- File Version 7.1.0.0
- Comments Symantec Application
- The loader module is a .Net executable that is obfuscated with ConfuserEx v1.0.0

2. Unpacked Modules
2.1. List of Unpacked Modules
Once we have executed the sample into the VM, we can check with Windbg that the malware unpacks a set of modules in memory:
After dumping these executables to disk we check that most of them are .Net executables, that we can decompile with dnSpy:
GrandSteal.* are the main modules of the malware. I uploaded the decompiled code for these modules to my GitHub. Additionally the malware carries some libraries that it will need.
2.2. Stealer
The malware contains code to steal credentials from different products:
2.2.1. Chromium Stealer
The malware is able to steal different information from Chromium Browsers:
The source code related to this functionality is ChromiumManager.cs.
The malware steals all the Chromium's information from the browser's sqlite database.
2.2.1.1. Cookies
It reads the cookies table from the sqlite database.
2.2.1.2. Credentials
It reads the logins table from the sqlite database.
2.2.1.3. Auto Fills
It reads the autofill table from the sqlite database.
2.2.1.4. Credit Cards
It reads the table credit_cards from the sqlite database.
2.2.2. Wallets Stealer
The malware is able to steal wallets from the following crypto-coin products:
- Litecoin: "%appdata%\Litecoin\wallet.dat"
- Litecoin-Qt: walletpath=read("HKCU\Software\Litecoin\strDataDir"), walletpath + "wallet.dat"
- Litecoin-Qt: walletpath=read("HKCU\Software\Litecoin-Qt\strDataDir"), walletpath + "wallet.dat"
- Bitcoin: "%appdata%\Bitcoin\wallet.dat"
- Bitcoin-Qt: walletpath=read("HKCU\Software\Bitcoin\strDataDir"), walletpath + "wallet.dat"
- Bitcoin-Qt: walletpath=read("HKCU\Software\Bitcoin-Qt\strDataDir"), walletpath + "wallet.dat"
- Bytecoin: "%appdata%\bytecoin\*.wallet"
- Exodus: "%appdata%\Exodus\*"
- Dash-Qt: walletpath=read("HKCU\Software\Dash\strDataDir"), walletpath + "wallet.dat"
- Dash-Qt: walletpath=read("HKCU\Software\Dash-Qt\strDataDir"), walletpath + "wallet.dat"
- Electrum: "%appdata%\Electrum\wallets\*"
- Ethereum: "%appdata%\Ethereum\wallets\*"
- Monero: walletpath=read("HKCU\Software\monero-project\wallet_path"), walletpath + "wallet.dat"
- Monero: walletpath=read("HKCU\Software\monero-core\wallet_path"), walletpath + "wallet.dat"
The source code related to this functionality is ColdWalletManager.cs.
2.2.3. Files From Personal Directories Stealer
The malware can steal files from Desktop, Favorites and Personal folders:
The source code related to this functionality is DesktopFileManager.cs.
2.2.4. Discord Software Stealer
From wikipedia: "Discord is a proprietary freeware VoIP application and digital distribution platform designed for video gaming communities, that specializes in text, image, video and audio communication between users in a chat channel".
The malware is able to steal information from this VoIP application by using a curious method. It calls DbgHelp.dll APIs (MiniDumpWriteDump) to create a minidump of any process containing the word "Discord" in the name.
Once the minidump file is created, it searchs the minidump for Discord json sessions by using a regex:
The source code related to this functionality is DiscordManager.cs.
2.2.5. FileZilla Stealer
The malware reads credentials from FileZilla XML files:
The source code related to this functionality is FileZillaManager.cs.
2.2.6. Gecko Stealer
From wikipedia: "Gecko is a browser engine developed by Mozilla. It is used in the Firefox browser, the Thunderbird email client, and many other projects".
The malware locates some Gecko important files:
It is able to recover credentials:
And cookies:
2.2.7. RDP Stealer
The malware can steal RDP credentials:
The source code related to this functionality is RdpManager.cs.
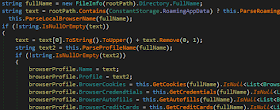
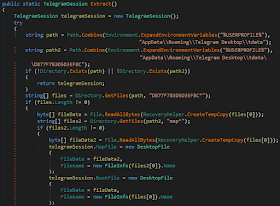
2.2.8. Telegram Stealer
The malware reads the files located at:
"%appdata%\Telegram Desktop\tdata\D877F783D5D3EF8C\map*"
From that files, it tries to recover Telegram sessions:
The source code related to this functionality TelegramManager.cs.
3. Yara Rules
rule grandsteal {
strings:
$s1 = "ws://{0}:{1}/websocket" wide
$s2 = "GrabBrowserCredentials: " wide
$s3 = "GrabColdWallets: " wide
$s4 = "GrabDesktopFiles: " wide
$s5 = "GrabTelegram: " wide
$s6 = "ColdWallets parser has been started" wide
$s7 = "DiscordSession parser has been started" wide
$s8 = "Rdps parser has been started" wide
$s9 = "DesktopFiles parser has been started" wide
$s10 = "FTPs parser has been started" wide
$s11 = "TelegramSession parser has been started" wide
$s12 = "ListOfProcesses parser has been started" wide
$s13 = "ListOfPrograms parser has been started" wide
$s14 = "card_number_encrypted" wide
$s15 = "\\Litecoin\\wallet.dat" wide
$s16 = "\\Bitcoin\\wallet.dat" wide
$s17 = "\\Exodus\\exodus.wallet" wide
$s18 = "\\Electrum\\wallets" wide
$s19 = "\\Ethereum\\wallets" wide
$s20 = "monero-project" wide
$s21 = "Discord dump UNKNOWN" wide
$s22 = "{0}\\FileZilla\\recentservers.xml" wide
$s23 = "{0}\\FileZilla\\sitemanager.xml" wide
$s24 = "cookies.sqlite" wide
$s25 = "password-check" wide
$s26 = "AppData\\Roaming\\Telegram Desktop\\tdata\\D877F783D5D3EF8C" wide
$s27 = "%USERPROFILE%\\AppData\\Local\\Temp\\Remove.bat" wide
$s28 = "taskkill /F /PID %1" wide
$s29 = "choice /C Y /N /D Y /T 3 & Del %2" wide
$s30 = "ExtractPrivateKey" wide
$s31 = "formSubmitURL" wide
$s32 = "passwordField" wide
$s33 = "usernameField" wide
$s34 = "GrabDiscord" wide
$s35 = "encryptedPassword" wide
$s36 = "masterPassword" wide
$s37 = "WalletName" wide
condition:
(30 of them)
}
4. Strings of the Main Unpacked Module
- https://domekan.ru/ModuleMystery/Updates.txt
- SQLite format 3
- ws://{0}:{1}/websocket
- Server is initialized
- CredentialsRequest has been created
- ParseClientSettings
- GrabBrowserCredentials:
- GrabColdWallets:
- GrabDesktopFiles:
- GrabTelegram:
- Invalid JsonMessage data from server. Exception :
- ClientInfos parser has been started
- ClientInfos has been parsed.Elapsed time: {0}
- Browsers parser has been started
- Browsers has been parsed.Elapsed time: {0}
- ColdWallets parser has been started
- ColdWallets has been parsed.Elapsed time: {0}
- DiscordSession parser has been started
- DiscordSession has been parsed.Elapsed time: {0}
- Rdps parser has been started
- Rdps has been parsed.Elapsed time: {0}
- DesktopFiles parser has been started
- DesktopFiles has been parsed.Elapsed time: {0}
- FTPs parser has been started
- FTPs has been parsed.Elapsed time: {0}
- TelegramSession parser has been started
- TelegramSession has been parsed.Elapsed time: {0}
- ListOfProcesses parser has been started
- ListOfProcesses has been parsed.Elapsed time: {0}
- ListOfPrograms parser has been started
- ListOfPrograms has been parsed.Elapsed time: {0}
- encrypted_value
- expiration_month
- expiration_year
- card_number_encrypted
- username_value
- password_value
- AppData\Roaming\
- AppData\Local\
- \Litecoin\wallet.dat
- \Bitcoin\wallet.dat
- \Exodus\exodus.wallet
- \Electrum\wallets
- \Ethereum\wallets
- monero-project
- JsonSession UNKNOWN
- Discord dump UNKNOWN
- Discord process UNKNOWN
- ({"token":"(.*)}}]})
- {0}\FileZilla\recentservers.xml
- {0}\FileZilla\sitemanager.xml
- cookies.sqlite
- [^\u0020-\u007F]
- password-check
- AppData\Roaming\Telegram Desktop\tdata
- AppData\Roaming\Telegram Desktop\tdata\D877F783D5D3EF8C
- D877F783D5D3EF8C*
- AppData\Roaming
- AppData\Local\Temp
- The binary key cannot have an odd number of digits: {0}
- %USERPROFILE%\AppData\Local\Temp\Remove.bat
- taskkill /F /PID %1
- choice /C Y /N /D Y /T 3 & Del %2
- ClientSettings.db
- 1.85 (Hash, version 2, native byte-order)
- FileDescription
- GrandSteal.Client.Data
- GrandSteal.Client.Data.dll
- ExtractPrivateKey3
- ExtractPrivateKey4
- get_formSubmitURL
- set_formSubmitURL
- GrandSteal.Client.Data
- RoamingAppData
- get_ObjectData
- set_ObjectData
- System.Collections.Generic
- Microsoft.VisualBasic
- get_ManagedThreadId
- get_CurrentThread
- get_timePasswordChanged
- set_timePasswordChanged
- get_timeLastUsed
- set_timeLastUsed
- get_timeCreated
- set_timeCreated
- HandleWorkCompleted
- OnWorkCompleted
- countCompleted
- OnResponseRecieved
- add_DataReceived
- add_MessageReceived
- System.Collections.Specialized
- get_passwordField
- set_passwordField
- get_usernameField
- set_usernameField
- BrowserCreditCard
- get_GrabDiscord
- get_encryptedPassword
- set_encryptedPassword
- get__masterPassword
- set_WalletName
- get_encryptedUsername
- set_encryptedUsername
- set_AllowUnstrustedCertificate
- DebuggerNonUserCodeAttribute
- DebuggableAttribute
- ComVisibleAttribute
- AssemblyTitleAttribute
- UserScopedSettingAttribute
- AssemblyTrademarkAttribute
- ExtensionAttribute
- AssemblyFileVersionAttribute
- AssemblyConfigurationAttribute
- AssemblyDescriptionAttribute
- CompilationRelaxationsAttribute
- AssemblyProductAttribute
- AssemblyCopyrightAttribute
- ConfusedByAttribute
- ParamArrayAttribute
- AssemblyCompanyAttribute
- RuntimeCompatibilityAttribute
- get_SQLDataTypeSize
- clientInfoFlag
- set_EnableAutoSendPing
- System.Threading
- get_DataEncoding
- FromBase64String
- DownloadString
- CreateTempPath
- get_ObjectLength
- set_ObjectLength
- set_ExpirationMonth
- get_Passwordcheck
- TransformFinalBlock
- ReadBrowserCredendtial
- ExtractManagerCredential
- ExtractRecentCredential
- op_GreaterThanOrEqual
- set_AutoSendPingInterval
- RuntimeTypeModel
- System.ComponentModel
- GrandSteal.Client.Data.dll
- BrowserAutofill
- get_BaseStream
- UserStreamParam
- ExceptionParam
- get_GrabTelegram
- SymmetricAlgorithm
- ICryptoTransform
- IsNullExtension
- DiscordSession
- discordSession
- TelegramSession
- telegramSession
- FindDiscordJsonSession
- GrandSteal.SharedModels.Communication
- set_ClientInformation
- RemoteClientInformation
- System.Configuration
- System.Globalization
- System.Reflection
- StringCollection
- MatchCollection
- CryptographicException
- ArgumentException
- GeckoPasswordBasedEncryption
- GrandSteal.Client.Models.Extensions.Json
- FileSystemInfo
- ProcessStartInfo
- GrandSteal.Client.Data.Gecko
- DeSerializeProto
- MiniDumpWriteDump
- set_ExpirationYear
- Key4MagicNumber
- set_CardNumber
- SHA1CryptoServiceProvider
- MD5CryptoServiceProvider
- TripleDESCryptoServiceProvider
- CrytoServiceProvider
- IFormatProvider
- FileZillaManager
- DiscordManager
- DesktopFileManager
- TelegramManager
- ChromiumManager
- ColdWalletManager
- ConvertToInteger
- ObjectIdentifier
- ResponseHandler
- System.CodeDom.Compiler
- ClientInfoHelper
- RecoveryHelper
- GrandSteal.Client.Data.Server
- InitializeServer
- CreateDecryptor
- System.Diagnostics
- AddMilliseconds
- timeoutMilliseconds
- get_BrowserCreditCards
- set_BrowserCreditCards
- GetCreditCards
- System.Runtime.InteropServices
- Microsoft.VisualBasic.CompilerServices
- System.Runtime.CompilerServices
- DebuggingModes
- get_ChildNodes
- get_BrowserCookies
- set_BrowserCookies
- get_Directories
- GetDirectories
- get_MasterEntries
- set_MasterEntries
- ExpandEnvironmentVariables
- Microsoft.Win32.SafeHandles
- set_DesktopFiles
- get_GrabDesktopFiles
- set_BrowserProfiles
- browserProfiles
- set_AutoAddMissingTypes
- ListOfProcesses
- RecieveSettings
- ClientSettings
- DataReceivedEventArgs
- MessageReceivedEventArgs
- ErrorEventArgs
- get_BrowserCredendtials
- set_BrowserCredendtials
- GrandSteal.Client.Models.Credentials
- SendCredentials
- rdpCredentials
- set_FtpCredentials
- ExtractFtpCredentials
- ftpCredentials
- get_GrabBrowserCredentials
- GetCredentials
- GrandSteal.SharedModels.Models
- GrandSteal.Client.Models
- GrandSteal.SharedModels
- get_BrowserAutofills
- set_BrowserAutofills
- GrandSteal.Client.Models.Extensions.Nulls
- set_InstalledPrograms
- ListOfPrograms
- GrandSteal.Client.Models.Extensions
- get_DesktopFileExtensions
- set_DesktopFileExtensions
- JsonExtensions
- ProtoExtensions
- get_DesktopExtensions
- set_DesktopExtensions
- RequestsExtensions
- System.Text.RegularExpressions
- System.Collections
- set_RdpConnections
- StringSplitOptions
- get_DesktopFileManagers
- get_RdpManagers
- get_FtpManagers
- get_BrowserCredentialsManagers
- get_ColdWalletManagers
- GrandSteal.Client.Data.Helpers
- RuntimeHelpers
- FindDisordProcess
- GetCurrentProcess
- set_ColdWallets
- get_GrabColdWallets
- get_disabledHosts
- set_disabledHosts
- GrabLitecoinQt
- CommunicationObject
- ReadTableFromOffset
- get__globalSalt
- get__entrySalt
- GetValueOrDefault
- CredentialManagement
- get_DocumentElement
- get_SqlStatement
- set_SqlStatement
- AutoResetEvent
- set_Screenshot
- CredentialsRequest
- set_ProcessList
- set_CreateNoWindow
- ConvertHexStringToByteArray
- InitializeArray
- FindValueByKey
- System.Security.Cryptography
- GetEntryAssembly
- CreateTempCopy
- GrandSteal.Client.Data.Recovery
- set_WorkingDirectory
- profilesDirectory
- GetCurrentDirectory
- GeckoRootEntry















Some on-line casinos additionally be} missing a small choice of games, however the majority of the gaming library shall be available immediately, or is within the means of being developed. Live vendor games mix the enjoyable and social elements of retail casinos with the convenience and velocity of on-line on line casino gaming. All bets are placed just about, and real cards are dealt from a reside vendor broadcasting reside from a studio positioned in the identical state you are be} wagering in. You can interact with the vendor and generally with different gamers just as you'll in 바카라 사이트 a retail on line casino environment, all out of your cellular device. New York handed a bill in 2013 that made sports gambling authorized at the state stage, however the state didn't open its first official sportsbook until July 2019. Mobile sports betting launched on January eight, 2022, and there second are|are actually} nine reside on-line sportsbooks within the Empire State.
ReplyDelete